Okta SSO
Rapticore identity federation and SSO
Rapticore uses AWS Cognito for authentication and authorization. It can Integrate with customer’s Okta identity provider using an Okta App configured in customer's account thereby providing SSO with Okta.
For more information on establishing trust between AWS Cognito and Okta, please refer to AWS documentation.
Setup
Setup involves configuration by both the customer and Rapticore. Configuration in Rapticore has already been taken care of. You need to perform the steps mentioned below and provision integration details to Rapticore:
Steps to be taken by customer include:
- Create an Okta app integration in your account
- Configure settings for your Okta app
- Provide integration details to Rapticore
Necessary privileges in Okta
A User with privileges to create and update Applications in Okta can complete the setup steps.
Rapticore information provided in your invitation email
Rapticore, at the time of account creation, will provide customers with two unique account attributes; both of these must be used without modification in the setup.
- RapticoreAccountId - Rapticore-operated AWS Account ID.
- RapticoreTenantId - Rapticore unique Tenant ID.
Create an Okta app integration
- Open the Okta Developer Console. For more information about the console, see [Okta’s Redesigned Admin Console and Dashboard—Now in GA!] (https://www.okta.com/blog/2021/04/oktas-redesigned-admin-console-and-dashboard-now-in-ga/) on the Okta Developer Blog.
- In the navigation pane, expand Applications, and then choose Applications. This opens the Applications Console. For more information, see [Administrator Console] (https://developer.okta.com/docs/concepts/okta-organizations/#administrator-console) on the Okta Organizations page of the Okta Developer website.
- Choose Create App Integration.
- On the Create a new app integration page, choose OpenID Connect, choose Web Application, and then choose Next.
Configure your Okta app
- On the New Web App Integration page, under General Settings, enter a name for your app, i.e., Rapticore.
- Under Grant type, confirm that the Authorization Code check box is selected. Your user pool uses this flow to communicate with Okta OIDC for federated user sign-in.
- For Sign-in redirect URIs, enter
https://auth.<RapticoreTenantId>.rapticore.io/oauth2/idpresponse. This is where Okta sends the authentication response and ID token.
Remember to replace <RapticoreTenantId> with your Rapticore Tenant ID.
<RapticoreTenantId> with your Rapticore Tenant ID.- Under CONFIGURE OPENID CONNECT, for Login redirect URIs, enter
https:// auth.<RapticoreTenantId>.rapticore.io/oauth2/idpresponse. This is where Okta sends the authentication response and ID token. - In Sign-out redirect URIs, add the URL
https://<RapticoreTenantId>.rapticore.io. - In Controlled access, choose your preferred access setting, and then choose Save.
- In Client Credentials, copy the Client ID and Client secret. These credentials are required by Rapticore to configure Okta in Amazon Cognito user pool.
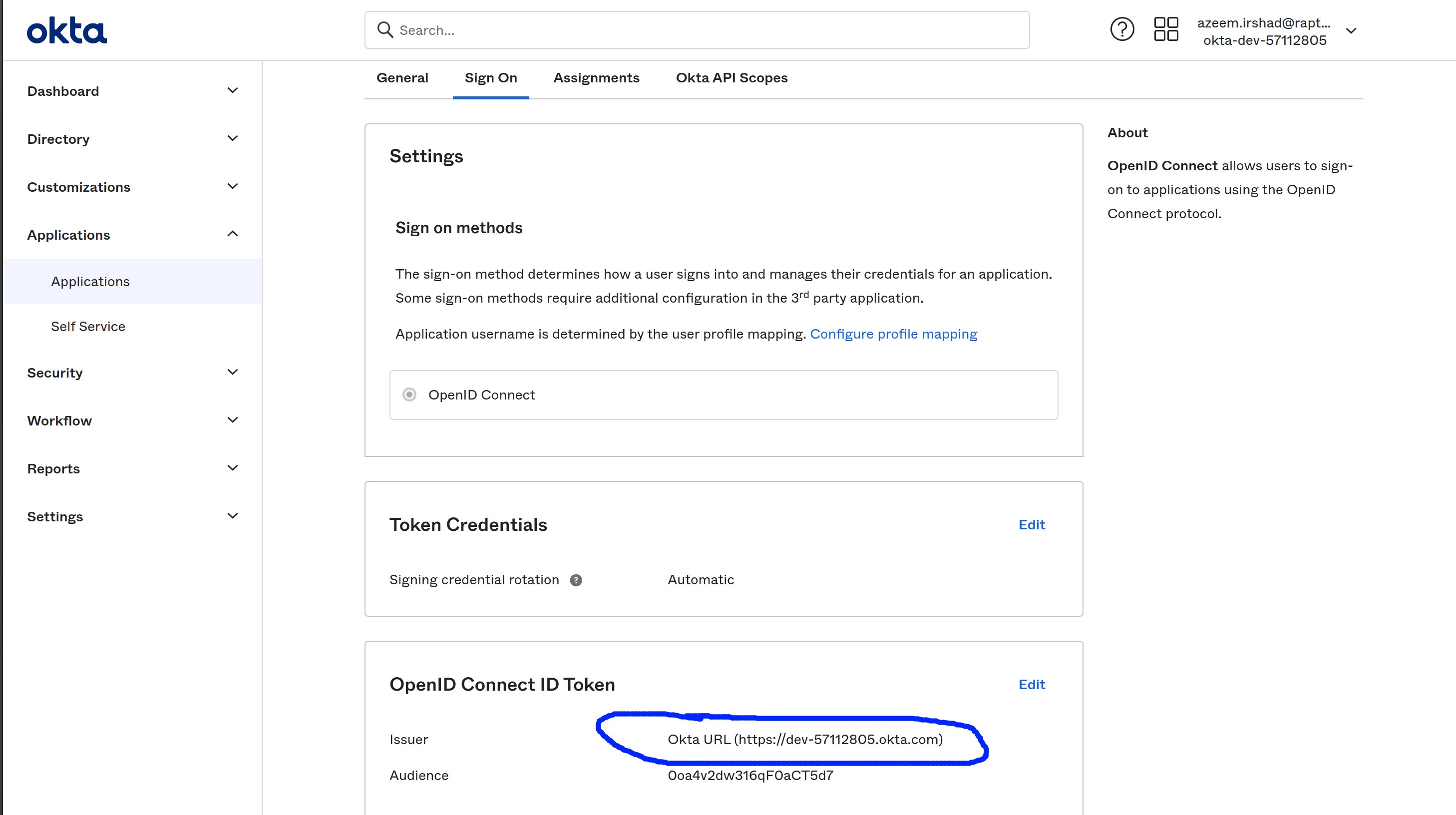
- Choose Sign On.
- On the Sign On page, In OpenID Connect ID Token, note the Issuer URL. This URL is required by Rapticore for configuring Okta in your user pool.
- Configure profile mapping
a. On Sign On page, click Configure Profile Mapping.
b. Ensure following mappings in Okta User to<Your Web App> tab:
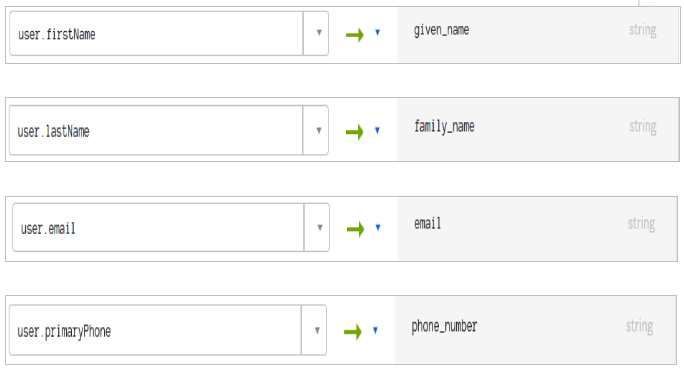
c. Click Save Mappings to save.
11. On web application detail page, open Okta API Scopes tab and ensure following scopes are granted:
a. okta.users.read
b. okta.users.read.self
c. okta.userTypes.read
d. okta.profileMappings.read
Provide integration details to Rapticore
Please provide the following once above steps are complete:
- Client ID
- Client Secret
- Issuer URL: Issuer URL can be obtained from "Sign On" tab in application detail page in Okta.
Wait for confirmation from Rapticore for configuring Okta SSO credentials.
Once this configuration is complete, users can click the Okta SSO button on Rapticore Login page to authenticate.
Decommissioning
Deactivating the Okta App created for Rapticore will stop Rapticore from authenticating users from Okta.
Changing the Attribute Mapping or Grants may affect the user authentication and authorization.
Updated about 1 year ago